Microsoft takes action against North Korea hackers
Hackers targeted US officials, think tanks, university staff and people working on nuclear technology
Microsoft is taking action against a North Korean hacking group it calls "Thallium."
A U.S. District Court issued a court order to the tech giant allowing it to take control of 50 web domains used by Thallium to hack into users' computers, the company said in a blog post on Monday.
Hackers targeted U.S. officials, think tanks, university staff, people working on nuclear technology and members of peace organizations, most of whom were based in the U.S. but some of whom were in Japan and South Korea, the company said.
Microsoft’s Digital Crimes Unit (DCU) and the Microsoft Threat Intelligence Center (MSTIC) have been tracking the group and discovered that they were operating a network of websites, domains and computers that they used to hack into victims' personal computers and gain access to their personal information.
Thallium attempted to trick victims by sending phishing emails, or emails that look legitimate and convince the user to click on a link, which then allows hackers to compromise and install malware on users' computers, according to Microsoft.
In one example, Microsoft shared an email that Thallium hackers sent to victims using an email address that appeared to be from "microsoft.com" but was actually from "rniscroft.com." By combining the letters "r" and "n" to appear as the "m" in Microsoft, hackers were attempting to trick users into clicking on a link that appeared to be from the U.S. tech giant, telling users that "unusual sign-in activity" had been detected on their accounts.
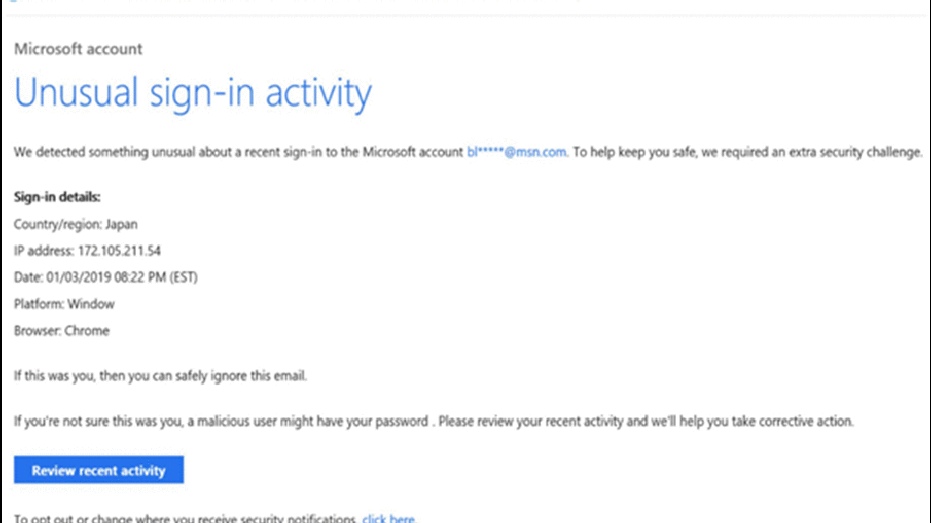
Phishing example/ Microsoft
The link would then redirect users to a website asking for their login credentials, which then allowed hackers access to computers and personal information. Thallium also installed malware called "BabyShark" and "KimJongRAT" on victims' devices, according to the post.
Microsoft has taken similar action against hacker groups in Russia, China and Iran, the post notes.




















